A few days ago I was browsing the world wide web, when suddenly I stumbled upon an article speaking about an IC sensor made by AMS, called the AS3935 Franklin Lightnin Sensor, which could detect the electrical signature of lightning strikes up to 40km and give the “strength” of the lightning as well as an estimation of the distance to the head of the storm. And all this in a tiny 4x4mm SMD circuit designed to be embedded in personal weather stations, watches, cars, etc.
My dark nerd side was tickled and I suddenly needed wanted to buy one and build a lightning detection station that could tweet about incoming storms, using my Raspberry Pi which is lying on a table doing nothing most of the time. And so I did it ! What I ended up with is a Twitter account on which lightning strikes info is tweeted in real time, with energy and distance estimation : https://twitter.com/toulouse_orages
After some research, I found that Embedded Adventure was selling a module with a pre-soldered sensor with the right antenna and components added to the board, ready to be used via an I2C interface. Some more research and I found that somebody already implemented a Python library to use such sensors on a Raspberry Pi. Perfect ! We have everything we need.

Wiring the sensor to the Raspberry Pi
Here is the wiring diagram to connect the sensor to the Raspberry Pi (you can use a different GPIO pin for the IRQ, but remember to change code accordingly):
| AS3935 Pin | MOD-1016 Pin | Raspberry Pi Pin |
|---|
| 4 (GND) | GND | 25 (Ground) |
| 5 (VDD) | VCC | 1 (3v3 Power) |
| 10 (IRQ) | IRQ | 11 (GPIO 17) |
| 11 (I2CL) | SCL | 5 (SCL) |
| 13 (I2CD) | SDA / MOSI | 3 (SDA) |
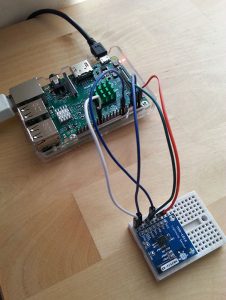
Here is a picture of my setup. For now, it’s just a quick prototype set up on a breakboard :
Writing the code to make it work
The Python library is pretty well self-documented, so just browse through the code and it should be enough. If you want to understand exactly how each of the sensor parameter works (Watchdog Threshold, Signal Rejection, etc, even some of which are not implemented in the library), refer to the AS9535 datasheet.
It could be useful to change those parameters that are not directly exposed, and it’s pretty easy to do so by directly calling RPi_AS3935.set_byte(register, value) (just be sure to call RPi_AS3935.read_data() first, and get the current value of the register so you only change the bits you need in it). For the Twitter part of the script, I chose to use the Tweepy module.
I just wanted to write a script that would listen for lightning, then tweet when a storm is happening. So first, to avoid getting false positives, I set the “minimum strikes” parameter to 5 (the sensor waits for 5 strikes in a predefined period before it starts sending IRQs for each subsequent strike). Then I have a handler which is run each time an IRQ is received. If it’s a strike, we tweet about it. But to avoid spamming tons of tweets, I set up a 5 minutes delay : if more than one strike happen during those 5 minutes, I’ll just tweet the number of strikes that have been detected. After 30min with no activity from the sensor, we can declare that the storm is over and tweet people that they should be okay now.
Here is an example tweet (yes it tweets in French, because I live in France. Baguette.) :
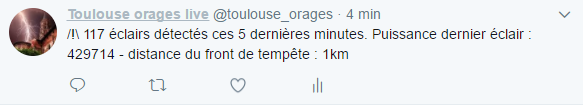
The translation would be “/!\ 117 strikes detected in the last 5 minutes. Power of the last strike : 429714 – distance to the head of the storm : 1km“.
As you can see, it was a pretty violent storm, with tons of intra-cloud strikes happening and being detected almost every other second (which is close to the maximum the sensor can detect, since in the datasheet we can read it waits for 1,5s after a strike has been detected and analyzed, before it starts listening again).
The Twitter account is : https://twitter.com/toulouse_orages
Final words
I had the chance to set it up right before a period of storms, here in Toulouse. At first I thought it might be crazy because it detected hundreds of strikes every few minutes. But no… it’s been 4 days now and I saw no false positives. The sensor didn’t detect any lightning for 48 hours, and started going crazy anytime a storm was approaching ! So I’m really happy with the results, that are much better than I would have thought from a little sensor like it. Especially since I didn’t take any time to calibrate it properly and mainly used factory settings. I just used the antenna capacitor tuning value given by Embedded Adventure, but it can be a good idea calibrating it again since temperature and other factors can influence it. A way to calibrate the antenna by reading the oscillation speed from the IRQ pin using an Arduino is explained here : as you can see, the process could be easily automatized.
If you’re interested in building your own station, you can find the final Python code for this bot on Github : Github – Hexalyse / LightningTweeter
Feel free to fork it, modify it and hack it to your needs ! If you have any question, remark or observation, do not hesitate to post a comment.
Hope you enjoyed 🙂 Happy storm-hunting !